Provided by HP
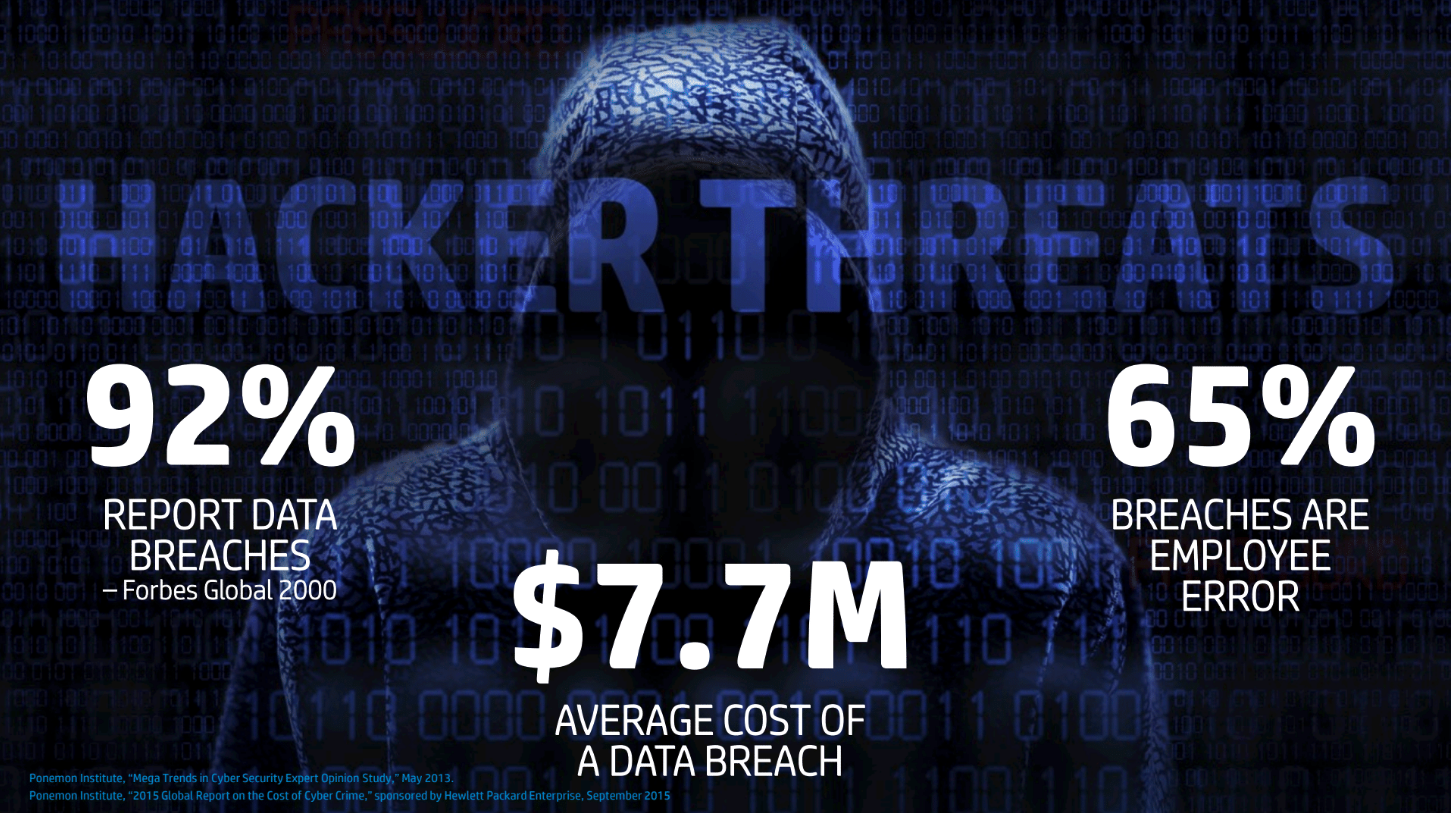
How are you protecting your organization, reducing your risk, while creating a cost effective Cyber Security program that helps grow your company and increases profits?
As a business owner or CXO this is a question most executives are constantly thinking about. Trying to maintain their compliance programs, regulations, client requirements, understanding the next generation solutions that could possibly help protect their organization from an active threat in your industry. How do you protect your business while focusing on the main responsibility of all CXO’s, increase profits while reducing the risk.
KNSS Consulting is here to provide consultative business first Cyber Security strategies. Our team is focused on helping you build your business while protecting it. Our consultative Cyber Security strategies work with you to understand your current business needs and design a Cyber Security roadmap that will grows with your organizations.
POTENTIAL SECURITY THREATS
939,722
Corporate Ransomware
Attacks 2017
240,000
Home User Ransomware
Attacks 2017
- Shoulder Surfing 19%
- Drive By Downloads 37%
- Phishing & Vishing Attacks 57%
- Malicious Email Attachments 65%
- Malicious Email Links 88%
OUR CYBER SECURITY STRATEGY
KNSS CONSULTING CYBERSECURITY SYSTEM
%
Cyber Security Gap Assessment
A Cyber Security Gap assessment needs to be our first stage to understand your organizations…
%
Cyber Security Maturity Program & Roadmap
The complexity of designing a business focused Cyber Security program is challenging as you know…
%
Deployment & Implementation
To provide your organization a holistic solution to help round out your current team if needed…
%
On-Going Care & Feed
This can be a daunting task especially depending on the size of your organization….
%
vCISO
The vCISO is designed to provide you a CISO who understands your business, the organizational risk and speaks to the board of directors…
Simple 5-Stage CyberSecurity Strategy
KNSS Consulting Group Inc. uses a simple 5-stage security strategy to help you stay protected. These stages are: Cyber Security Gap Assessment, Customized Cyber Security Maturity Program & Roadmap, Deployment & Implementation, On-Going Care and Feed, and Virtual Chief Information Officer. These strategy are designed to provide a completely Cyber Security program to help you reduce your risk while increasing profits.
Stage #1 Cyber Security Gap Assessment
A Cyber Security Gap assessment needs to be our first stage to understand your organizations current security posture, vulnerabilities, industry requirements and risk. This will give us a baseline of your current security posture in relation to your industry standards and compliance. With this information the Cyber Security program will be designed to help protect your business and not hinder your organizations growth .
Stage #2 Customized Cyber Security Maturity Program & Roadmap
The complexity of designing a business focused Cyber Security program is challenging as you know. Most security strategies and/or solutions restrict business functionality to help protect the organization. Focusing on protecting the confidentiality and integrity of the business, which as you know reduces the availability of easy to use business systems. This is why our team focuses on building a Cyber Security Maturity program and roadmap that understands the businesses functionality, systems, as well as processes that need to be accessible to grow the business.
Stage #3 Deployment & Implementation
Depending on the size of your organization and the resources you have available to you, we will work with your team to deploy as well as implement your Cyber Security program. This can consist of Governance, Compliance, policies, procedures and guidelines to technical security controls. Our team provides your organization a holistic solution to securing your company. We have partnered up with a Managed Service Providers and Managed Security Service Providers to help round out your current team if you need additional resources.
Stage #4 On-Going Care and Feed
With many Cyber Security program there is on-going care and maintenance that is necessary to maintain your security posture. With the amount of projects as well as transitions most organizations are constantly going through. This can be a daunting task especially depending on the size of your organization. We provide Managed services that help your organizations to monitor, patch, remediate and manage your Cyber Security program. Our MSP, MSSP and MGRC partnerships will provide the level of service you need to protect your organization.
Stage #5 Virtual Chief Information Security Officer
The new Virtual Chief Information Security Officer “vCISO” is designed to provide you a CISO who understands your business, the organizational risk and speaks to the board of directors, investors, as well as the executives about the Cyber Security program for your organizations at a business level.
ABOUT US
The KNSS Consulting Team is here to help you. With over 20+ combined years of experience, we understand how hard it is to grow your business and maintain a Cybersecurity posture in the ever transitioning environment. We constantly work with Business owners and CXO’s to strategize their business and Cyber Security needs, as well as requirements. We are constantly staying up to date on the newest Cyber Security solutions, defense in-depth strategies and sharing these with our clients. We are passionate about business and Cyber Security!

Brandon Krieger:
Is the President of KNSS Consulting Group and vCISO, focus on helping organizations across North America grow as well as protect their organizations from the current Cyber Security risks. Brandon works with a team of Cyber Security experts to provide organizations defense in-depth cybersecurity services, as well as solutions that reduce risk, while increasing profits.
Brandon’s passion is to help organizations across North America protect their employees, clients, shareholders and business partners from the Cyber Security threats we are all facing.
For more information please contact Brandon below.
Our Clientele
Our experience is derived from a combination of our years of experience in the industry and what we have learned from our clients. We have had the great pleasure of working with a wide variety of clients from all types of industries, some of which are listed below. We are fortunate to have worked with such a variety of clients from all of the industries below.
Our Clientele
Our experience is derived from a combination of our years of experience in the industry and what we have learned from our clients. We have had the great pleasure of working with a wide variety of clients from all types of industries, some of which are listed below. We are fortunate to have worked with such a variety of clients from all of the industries below.
Insurance
Lawyers
Education
Accountants
Entreprenuers
Financial
Franchises
Restaurants
Business Consultants
Medical
Dental
Technology
Health and Wellness
Retail
Automotive
CONTACT US TODAY FOR MORE INFORMATION
Headquarters
Headquarters
More Info: We want to help you protect your profits and organization today! Fill out the contact form and we will get back to you within 24 hours.
Address: 2969 Bloor Street West Etobicoke, ON, M8X 1B8
Phone: 416-239-9351
Business Hours:
9am–5pm Mon – Thur
