Have any of your smart phones, credit card, e-mail, website, T.V.’s or other electronic devices been hacked? Can they be? Do any of the apps you have downloaded have bugs, spyware, geo tracking, hacks or any obtrusive aspects that you don’t even know about?
As a business owner I am sure you use most of these technologies daily. There are even applications like CRM’s, list building tools, social sites, websites…etc that you use to build your business. What if I told you that these tools can be what is opening you up to be vulnerable for an attack. Yes even a small mom and pop shop can be attacked.
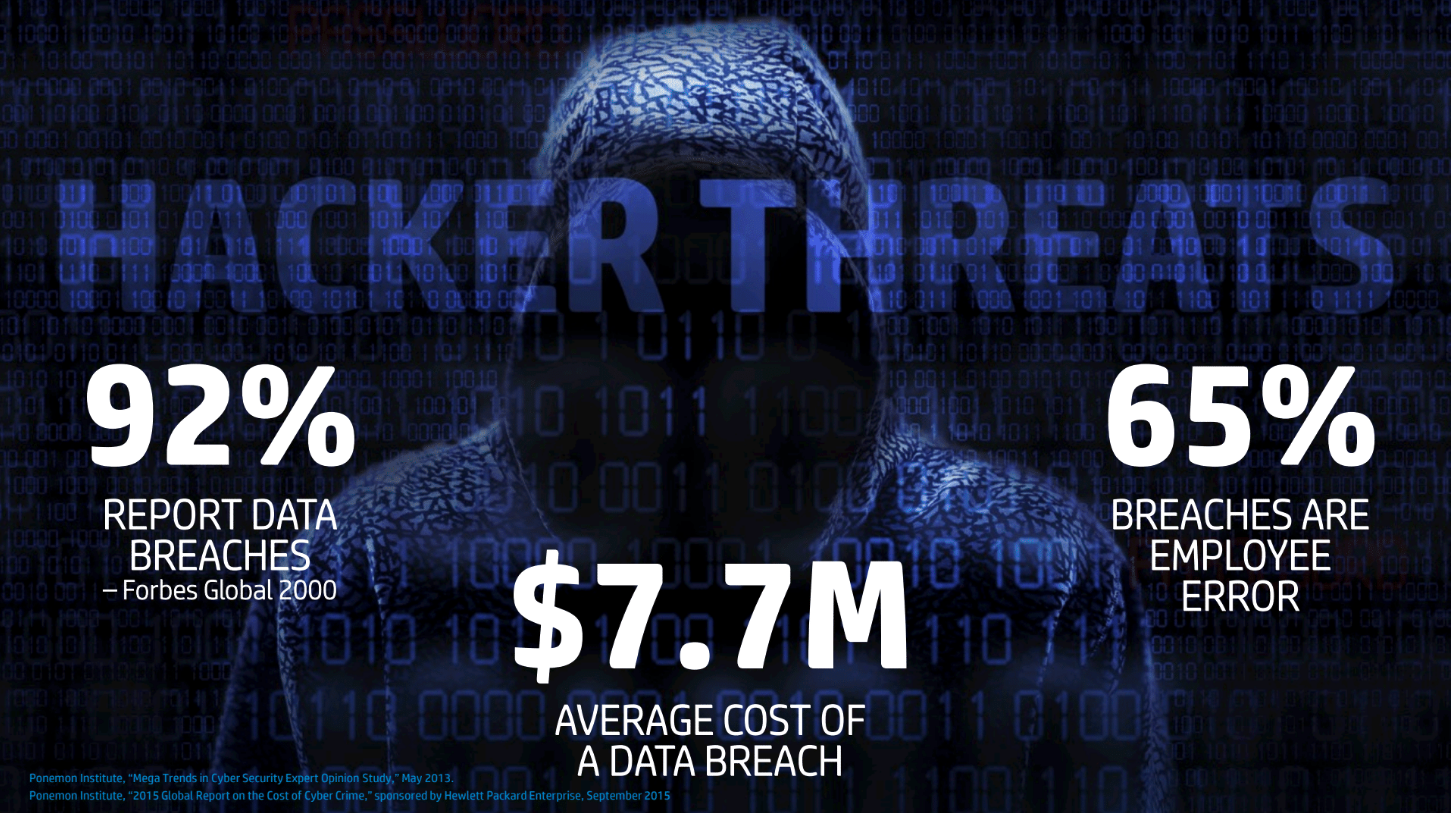
Do not think because you are a small business that you can not be compromised? Spyware, malware, bugs, social engineering, …etc look for vulnerabilities to gain access to you and your important information – no matter what size of business you are in. In 2015 there where over 75 million peoples’ personal identifiable information stolen (PII). That includes credit card, bank accounts, birth certificates, social insurance/social security numbers…etc from major corporations who spend millions on Cybersecurity. This is predicted to increase in 2016.
Don’t be one of the 75+ million that will potentially get compromised in 2016. Learn how you can be pro-active and protect your business and your clients’ information.
Join the KNSS Cybersecurity Community and get the answers and solutions to these and any other security concerns you have or may not even know you have.
POTENTIAL SECURITY THREATS
939,722
Corporate Ransomware
Attacks 2017
240,000
Home User Ransomware
Attacks 2017
- Shoulder Surfing 19%
- Drive By Downloads 37%
- Phishing & Vishing Attacks 57%
- Malicious Email Attachments 65%
- Malicious Email Links 88%
WHAT IS CYBERSECURITY?
Cyber Security Is:
Cyber Security is the ability to protect or defend the use of cyberspace from cyber-attacks.
When you think of cyberspace think of; website, social media, email, e-commerce, cloud storage/solutions…etc. Each of these cyber properties need to be hardened (secured) to protect the C.I.A. triad, which stands for Confidentiality, Integrity of your data, and Availability.
Confidentiality is the focus of protected and keeping your data private. It is essential that you keep your information secure from un-authorized users. With the increase of cyber attacks focused on stealing your data, it is essential you have systems in place to protect your data.
Integrity of your data is the process of protected your information from being tampered as well confirming the integrity of the data either in transit or at rest in a stored location.
Availability is important because you want your systems to be available to your staff, vendors, suppliers, and clients when they needs access to it. If your systems are down that effects your productivity, has a financial impact and effects your brand.
It’s important for all companies of any size to make cyber security a priority in your business.
KNSS CONSULTING CYBER SECURITY SYSTEM
KNSS Consulting Group 5-Stage Security Strategy
KNSS Consulting Group Inc. uses a 5-stage security strategy to help you stay protected. These stages are: baseline assessment, security policies & procedures, education, cyber security systems, and on-going maintenance. This strategy is on-going and needs to be constantly maintained to make sure you stay protected.
Stage #1 Baseline Assessment
A baseline assessment needs to be our first stage to see where your corporation is vulnerable to attacks. This is known in the industry as a penetration test. This is essential to make sure that all vulnerabilities are recorded and addressed.
Stage #2 Security Policies and Procedures
Security policies and procedures need to be written to help protect your corporation, as well as provide guidelines on what to do when your corporation gets compromised by a cyber security attack. These policies and procedures are essential to your cyber security strategy.
Stage #3 Education
Education is an essential and on-going strategy. With cyber security attacks constantly changing and your corporation being attacked from all sides your entire team needs to be constantly trained and updated on current threats.
Stage #4 Cyber Security Systems
Cyber security systems are required to help protect your; data, systems, staff and you from potential attacks. These systems are in place to monitor, alert, notify and help you recover when there is a cyber security attack. Examples of a few of these systems are patch management, back-ups, anti-virus, anti-malware, and security monitoring software.
Stage #5 On-going Maintenance
On-going maintenance is the last and most important stage to maintaining your cyber security strategy. With technologies constantly changing, companies updating their software and hackers coming out with new ways to compromise companies. It is important for your cyber security strategy to stay up to date and be maintained.
CONTACT US TODAY FOR MORE INFORMATION
Headquarters
More Info: We want to help you grow your business. Fill out the form on the left side and we will get back to you within 24 hours.
Address: 2969 Bloor Street West Etobicoke, ON, M8X 1B8
Phone: 416-239-9351
Business Hours:
10am–5pm Mon – Thur
